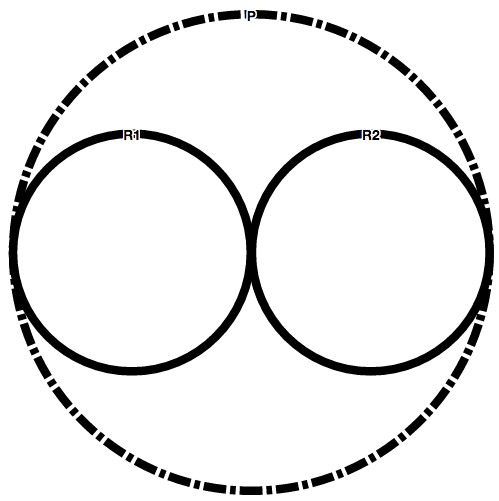
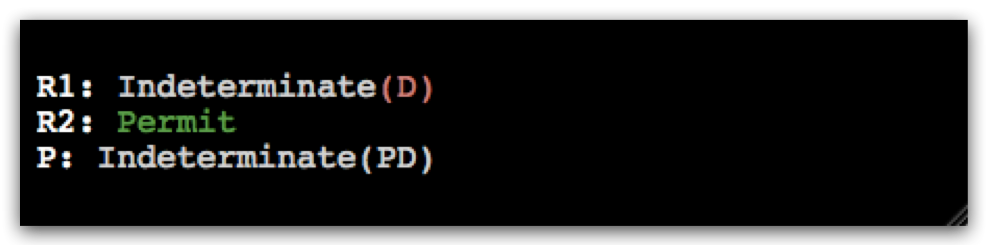
The following sub-sections show the most common composition operators used in access control policies. Please notice that not all of the operations are commutative (Not all tables are symmetrical).
Please bear in mind that VisABAC uses line conventions to represent different composition operators.
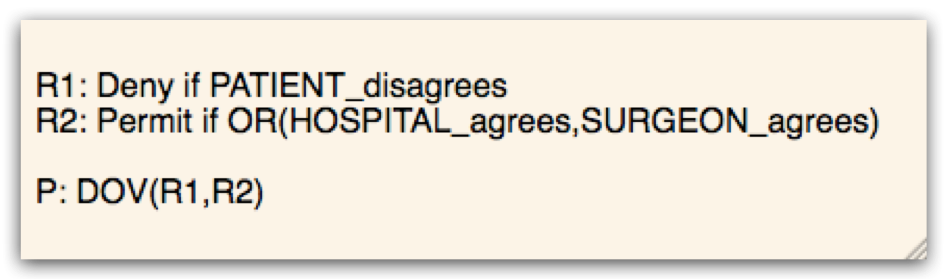
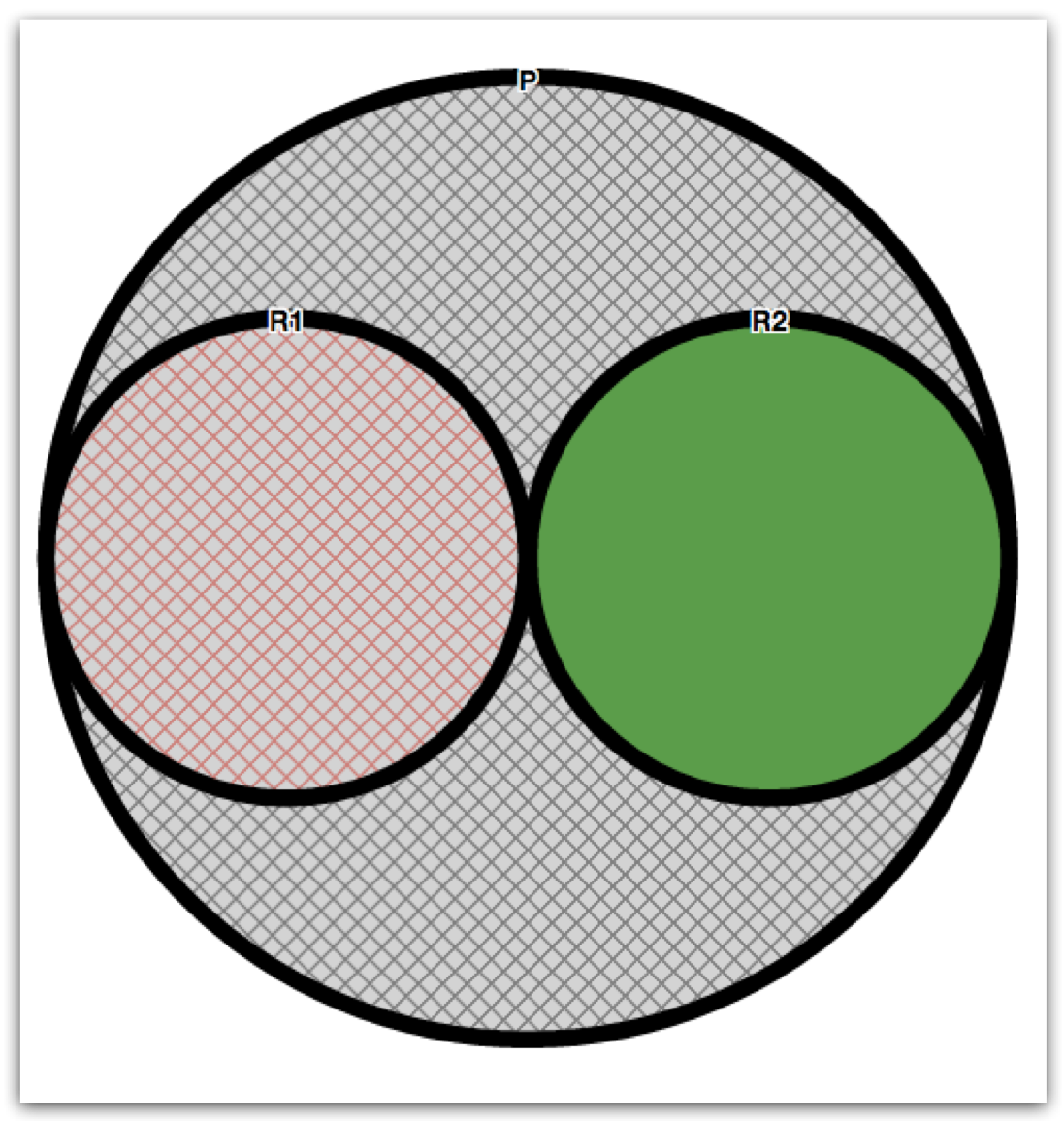
Deny-Overrides
| DOV | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
|---|---|---|---|---|---|---|
| Permit | Permit | Deny | Permit | Permit | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
| Deny | Deny | Deny | Deny | Deny | Deny | Deny |
| Not Applicable | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit) | Permit | Deny | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Deny) | Indeterminate (Permit-Deny) | Deny | Indeterminate (Deny) | Indeterminate (Permit-Deny) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Deny | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
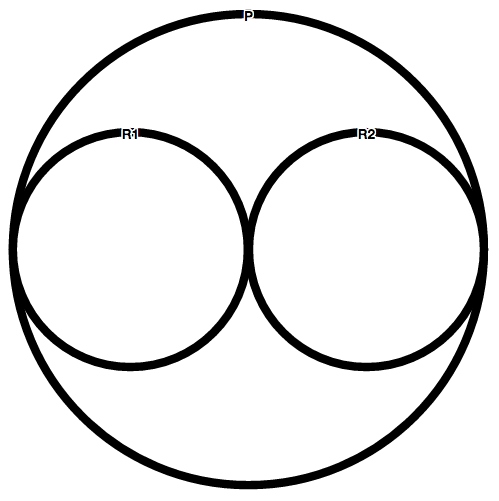
Visual Representation
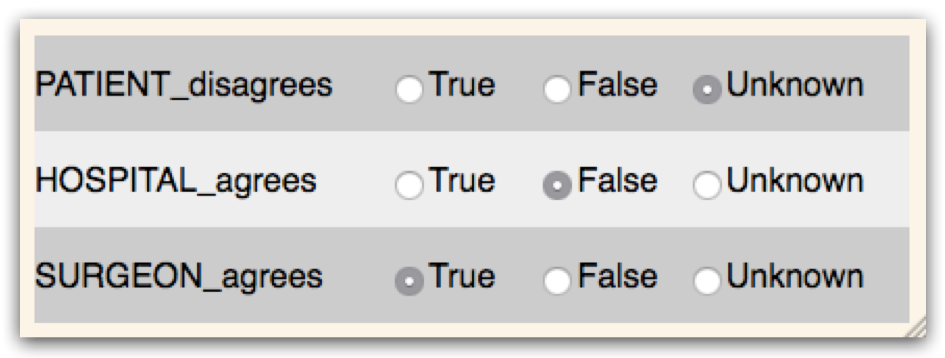
Given the following policy P=DOV(R1,R2) where {R1,R2:not applicable}; P is represented by the following line:
Permit-Overrides
| POV | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
|---|---|---|---|---|---|---|
| Permit | Permit | Permit | Permit | Permit | Permit | Permit |
| Deny | Permit | Deny | Deny | Indeterminate (Permit-Deny) | Deny | Indeterminate (Permit-Deny) |
| Not Applicable | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit) | Permit | Indeterminate (Permit-Deny) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Deny) | Permit | Deny | Indeterminate (Deny) | Indeterminate (Permit-Deny) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit-Deny) | Permit | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
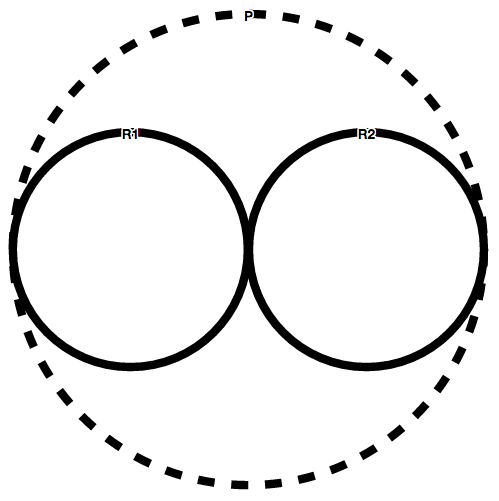
Visual Representation
Given the following policy P=POV(R1,R2) where {R1,R2:not applicable}; P is represented by the following line:
Deny-Unless-Permit
| DUP | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
|---|---|---|---|---|---|---|
| Permit | Permit | Permit | Permit | Permit | Permit | Permit |
| Deny | Permit | Deny | Deny | Deny | Deny | Deny |
| Not Applicable | Permit | Deny | Deny | Deny | Deny | Deny |
| Indeterminate (Permit) | Permit | Deny | Deny | Deny | Deny | Deny |
| Indeterminate (Deny) | Permit | Deny | Deny | Deny | Deny | Deny |
| Indeterminate (Permit-Deny) | Permit | Deny | Deny | Deny | Deny | Deny |
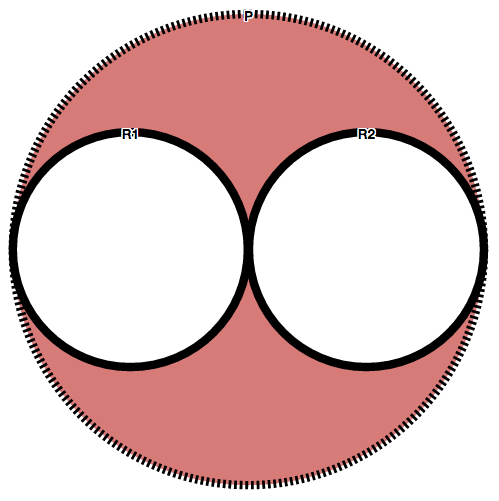
Visual Representation
Given the following policy P=DUP(R1,R2) where {R1,R2:not applicable}; P is represented by the following line:
Permit-Unless-Deny
| PUD | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
|---|---|---|---|---|---|---|
| Permit | Permit | Deny | Permit | Permit | Permit | Permit |
| Deny | Deny | Deny | Deny | Deny | Deny | Deny |
| Not Applicable | Permit | Deny | Permit | Permit | Permit | Permit |
| Indeterminate (Permit) | Permit | Deny | Permit | Permit | Permit | Permit |
| Indeterminate (Deny) | Permit | Deny | Permit | Permit | Permit | Permit |
| Indeterminate (Permit-Deny) | Permit | Deny | Permit | Permit | Permit | Permit |
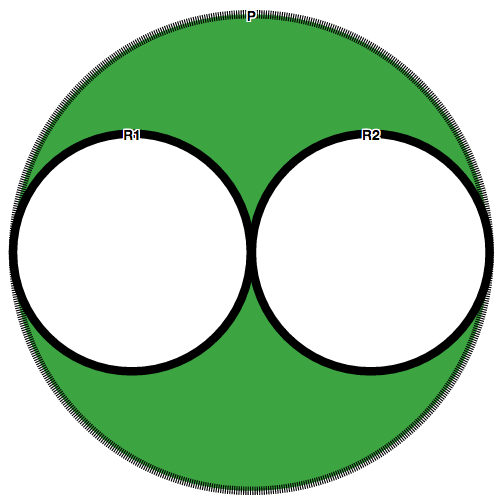
Visual Representation
Given the following policy P=PUD(R1,R2) where {R1,R2:not applicable}; P is represented by the following line:
First-Applicable
| FA | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
|---|---|---|---|---|---|---|
| Permit | Permit | Permit | Permit | Permit | Permit | Permit |
| Deny | Deny | Deny | Deny | Deny | Deny | Deny |
| Not Applicable | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) |
| Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) |
| Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
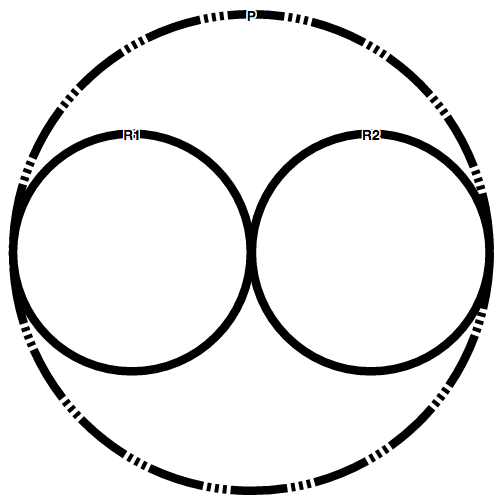
Visual Representation
Given the following policy P=FA(R1,R2) where {R1,R2:not applicable}; P is represented by the following line:
Only-One-Applicable
| OOA | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
|---|---|---|---|---|---|---|
| Permit | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Permit | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Deny | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Deny | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Not Applicable | Permit | Deny | Not Applicable | Indeterminate (Permit) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Deny) | Indeterminate (Permit-Deny) | Indeterminate (Deny) | Indeterminate (Permit-Deny) |
| Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) | Indeterminate (Permit-Deny) |
Visual Representation
Given the following policy P=OOA(R1,R2) where {R1,R2:not applicable}; P is represented by the following line: